- 28 Posts
- 20 Comments
I was concerned that we would now have five competing databases, each with their own, inconsistent data.

 3·22 days ago
3·22 days agoI’ve got it running for a few weeks now. Seems very nice

 112·22 days ago
112·22 days agoNice list of suggestions, but implementing all of them feels a little over-the-top.

 41·22 days ago
41·22 days agoI don’t really get the love for fail2ban. Sure, it helps keep your logs clean, but with a solid SSH setup (root disabled, SSH keys enforced), I’m not bothered by the login attempts.

 5·25 days ago
5·25 days agoThe current tariff approach by the republican administration does not include the tariffs on US exports. They are not included in the formula.

 37·1 month ago
37·1 month agoTeams randomly selects the wrong microphone, so either people can’t hear me or they can hear everyone around me too (laptop mic).
How hard can it be to store my microphone preference?
This week, I’ve been trying out caddy + coraza web app firewall. I got it to work, I’m planning to use it for my homeserver.

 8·1 month ago
8·1 month agoI’m currently comparing Authentik and Authelia. For me, Authentik was extremely easy to get into. Authelia with its text-based configuration is clearly not as easy for beginners.
Dismantle them and build them new inside the bottle probably

 2·4 months ago
2·4 months agoWith Ivanti VPN, attackers can transfer your data to the darknet over an encrypted connection.

 1·4 months ago
1·4 months agoObvoiusly companies need some data, both for practical and legal requirements.
But tracking every start and stop of a car with 1 meter accuracy meets none of these requirements. This is just a needless risk for everyone involved.
Security by old software, or how I call it: the ivanti approach
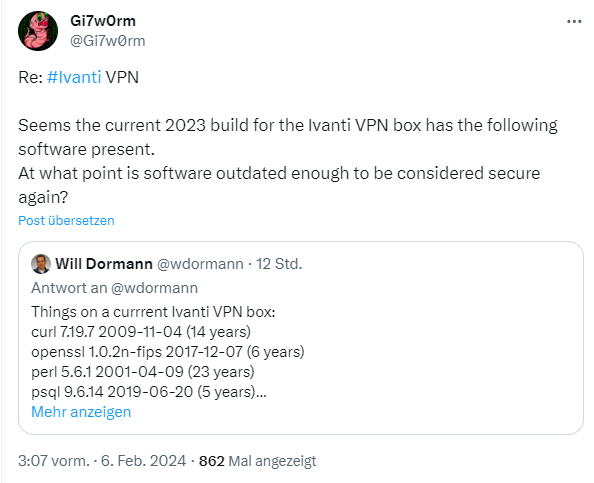

 1·8 months ago
1·8 months agoNice new name:
The company now legally known as “THAT COMPANY WHOSE NAME USED TO CONTAIN HTML SCRIPT TAGS LTD”
Not LLMs (Large Language Models). ReCaptcha by Google was used to improve image and text recognition AI.
They’re too special.

 1·8 months ago
1·8 months agoI did it both ways, but I wanted to post the more positive version.

Carry a ladder and a toolbox and everyone will open the door for you.
OWASP recommendation is to allow 64 chars at least:
Maximum password length should be at least 64 characters to allow passphrases (NIST SP800-63B). Note that certain implementations of hashing algorithms may cause long password denial of service.
The lemmy-UI limit is reasonably close and as everything is open source, we can verifiy that it does hash the password before storing it in the database.
There is a github issue, too.
Please add kaspersky, symantec, zone alarm and trend micro to make sure you have
all the backdoors100% security.




True. Additionally, some might be embarrassed or too afraid to report an incident.